Back to Cyber Security Basics: The Importance of Good Cyber Hygiene for Private Equity Firms
September 6, 2024
Organisations can often equate cyber security with a toolkit. More tools, they believe, equals greater protection. However, it is crucial to resist the allure of “shiny new toys”. While cyber security tools are valuable and constantly improving, they are not a magic fix.
OneCollab simplifies cyber security by helping private equity firms implement effective cyber hygiene practices. Returning to cyber security basics is essential for protecting your organisation’s sensitive information. Good cyber hygiene practices are the foundation for any robust security posture. Every organisation, regardless of size, budget, or industry, must embed these practices into daily operations.
Private equity firms face unique cyber security challenges due to the consolidation of multiple companies, often with diverse IT systems and security practices. This complexity increases the attack surface, making it easier for cybercriminals to exploit vulnerabilities.
Research from the Ponemon Institute indicates the average enterprise now manages approximately 135,000 endpoints. Worryingly, nearly half (48%) of these devices are at risk because they are undetected by IT or have outdated operating systems. 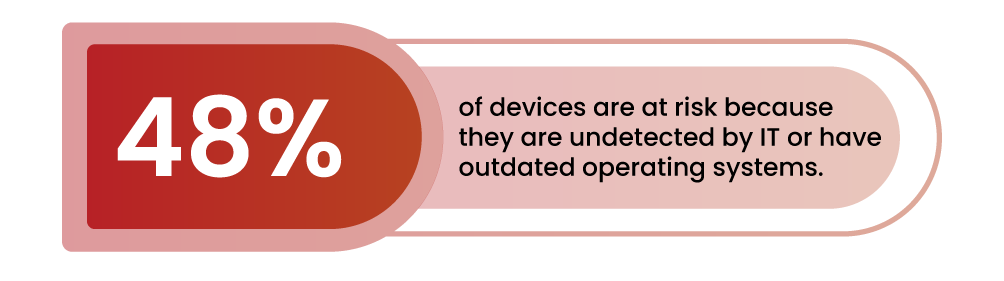 This, along with the growth of cloud services that allow access from anywhere, creates a web of interconnected devices with numerous potential entry points for attackers. With that many potential points of entry, we all must ensure that, besides having the right cyber security tools, we are sticking to fundamental, tried-and-true cyber hygiene practices to limit the risk of attack, speed the process of detection, and ensure reliable, consistent remediation.
This, along with the growth of cloud services that allow access from anywhere, creates a web of interconnected devices with numerous potential entry points for attackers. With that many potential points of entry, we all must ensure that, besides having the right cyber security tools, we are sticking to fundamental, tried-and-true cyber hygiene practices to limit the risk of attack, speed the process of detection, and ensure reliable, consistent remediation.
Cyber security is complex. But, by implementing these five core cyber security basics, you can make it simple.
Maintaining up-to-date software is essential for protecting your organisation and your portfolio companies. Implement a robust patching process to address vulnerabilities promptly. Cybercriminals often exploit these weaknesses, so it is crucial to stay ahead of threats.
To ensure comprehensive protection for your portfolio, focus on these key steps:
Data loss can be catastrophic for any organisation, especially in private equity. To protect critical information and ensure business continuity, a robust backup strategy is essential.
Automated backups are crucial for efficient and reliable data protection. By automating the backup process, organisations can significantly reduce the risk of human error and ensure that data is consistently protected.
Adhering to the 3-2-1 backup rule is a best practice for data redundancy and security. This strategy involves creating at least three copies of data, storing two copies on different media (e.g., internal, and external hard drives), and keeping one copy offsite or in the cloud.
By following these guidelines, organisations can significantly reduce the risk of data loss and maintain business operations in the event of a disaster.
Proactive vulnerability management is vital for reducing cyber risks. Private equity firms should carry out regular vulnerability scans to identify and address potential weaknesses in their systems and applications. These scans should be performed at intervals aligned with available resources and internal processes.
To minimise risk and protect investments, private equity firms should prioritise the following;
The exposure of privileged credentials can be a significant security vulnerability. If a malicious actor obtains a credential with administrative privileges, they can freely move through your entire environment, leaving minimal traces.
It is common to see organisations granting administrative privileges without implementing adequate controls. The correct process should include:
Additionally, it is crucial to promptly revoke administrative privileges when a user leaves the organisation or no longer needs them. Ensure you have the necessary mechanisms in place to facilitate privilege revocation requests promptly.
What happens if a malicious actor breaches your organisation or one of your portfolio companies and compromises sensitive data? How would your IT team respond? What are your containment plans, and when should they be implemented?
These questions are central to an effective risk management strategy. Your IT team must be prepared for potential breaches and outages by developing comprehensive incident response plans. While risks cannot be eliminated, understanding them is essential for mitigating their impact.
As part of your strategy, it is also crucial to effectively manage third-party risks. Ensure that your vendors adhere to the same high security standards as your organisation. Request and review their cyber security policies and procedures to assess the adequacy of their security measures.
While the five foundational components of cyber hygiene are essential, a critical aspect often overlooked is the ongoing management and execution of cyber security solutions.
To ensure the effectiveness of your cyber security strategy, it is essential to invest in dedicated resources and personnel to oversee its implementation. Without proper management, critical security events and issues may be overlooked or ignored.
By implementing a comprehensive cyber security strategy, practicing good cyber hygiene, and actively managing its execution, private equity firms can significantly reduce their risk of falling victim to cyber threats.
Cyber security can be complex and overwhelming, especially for private equity firms managing multiple companies with diverse IT systems. At OneCollab, we specialise in providing bespoke cyber security solutions that address the unique challenges faced by Private Equity firms.
Our expert team can help you:
Contact us today for a free consultation and discover how we can help you achieve a robust and effective cyber security posture.
Cyber security shouldn’t be a headache. Get clear and actionable insights delivered straight to your inbox. We make complex threats understandable, empowering you to make informed decisions and protect your business.
Call us +44 20 8126 8620
Email us [email protected]