Understanding the Security Risks of QR Codes
November 28, 2023
QR codes have become widespread, playing a crucial role in our smartphone-driven world. They offer seamless access to information and services, from event passes and restaurant menus to supply chain product tracking and business payments. However, their widespread use has attracted cybercriminals, making QR codes a target for phishing and malware attacks.
In this article, we simplify the complexities of QR code security, expose real-world scam techniques, and provide insights to enhance cyber security measures for both individuals and businesses.
QR codes, often compared to 3D barcodes, feature a distinctive square pattern that allows them to store extensive data, unlike traditional barcodes limited to short alphanumeric strings.
A primary application of QR codes is in advertising, where their ability to hold lengthy information, such as URLs, is invaluable. In our smartphone-centric world, QR codes enable instant access to websites without the need to manually enter web addresses. Advertisers leverage this by placing QR codes on billboards, in magazines, at trade shows, and other high-visibility locations.
For organisations, QR codes are powerful tools to measure the effectiveness of advertising campaigns. By using unique QR codes for different ad placements, companies can track which codes are scanned and identify the most engaging advertisements. This data-driven approach allows for precise analysis of audience interest and campaign performance.
QR codes are appealing to cybercriminals for several reasons. They can seamlessly replace traditional URL links or file attachments in emails. When scanned, QR codes direct users to specific websites or activate specialised apps, allowing attackers to obscure phishing URLs and malware downloads, often bypassing email gateways and anti-phishing cybersecurity tools.
The unassuming nature of QR codes makes them ideal for concealing malicious content. While users may be cautious of suspicious URLs and dubious links, QR codes often escape scrutiny due to their benign appearance. As familiarity with QR technology grows, users may lower their guard, increasing their vulnerability to threats that would be more apparent with traditional links.
Additionally, QR codes are primarily designed for smartphone use. When an email is opened on a desktop, users often switch to a less secure personal device, like a smartphone, for QR code scanning, especially in remote work settings. This transition can expose users to greater risks compared to accessing potentially malicious links on their more secure primary devices.
QR code scammers use various tactics to deceive and exploit victims. Here are some of the most prevalent techniques:
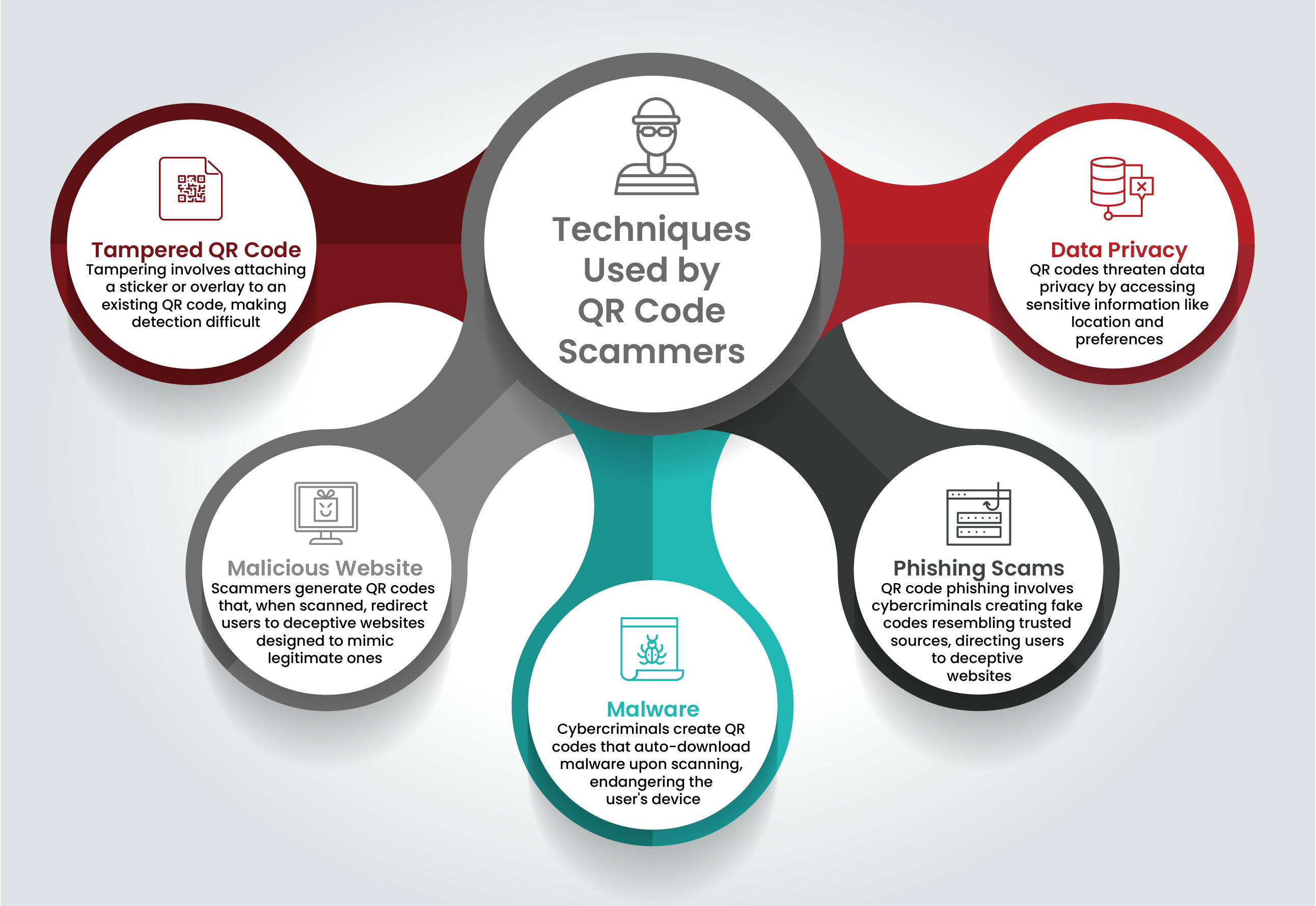
Cybercriminals can easily tamper with QR codes by overlaying a sticker or an overlay onto an existing code, redirecting users to malicious websites or initiating malware downloads. This makes it challenging to detect the manipulation.
Scammers create QR codes that redirect users to deceptive websites designed to mimic legitimate ones. Users may unknowingly enter sensitive information, such as login credentials, which cybercriminals then use for fraudulent activities.
QR codes can serve as vectors for malware distribution. Scanning a malicious QR code can trigger automatic malware downloads, compromising the user’s device and potentially infecting other devices on the same network.
Phishing is another significant risk. Scammers produce counterfeit QR codes resembling those from trusted sources, like banks or government agencies. Scanning these fake codes directs users to fraudulent websites that request personal information, which can be exploited for identity theft and other fraudulent activities.
Scanning a QR code can grant access to sensitive information, such as location data or personal preferences. Hackers can use this data to track users’ activities or steal personal information, compromising data privacy.
Understanding these common techniques allows individuals and businesses to take proactive measures to enhance their QR code security. Staying informed and adopting cyber security best practices is essential to maintaining the utility and safety of QR codes.
Cybercriminals use QR codes to lure victims into accessing fake websites or downloading malicious software. To protect yourself and your firm, it’s crucial to understand the various types of QR code scams:
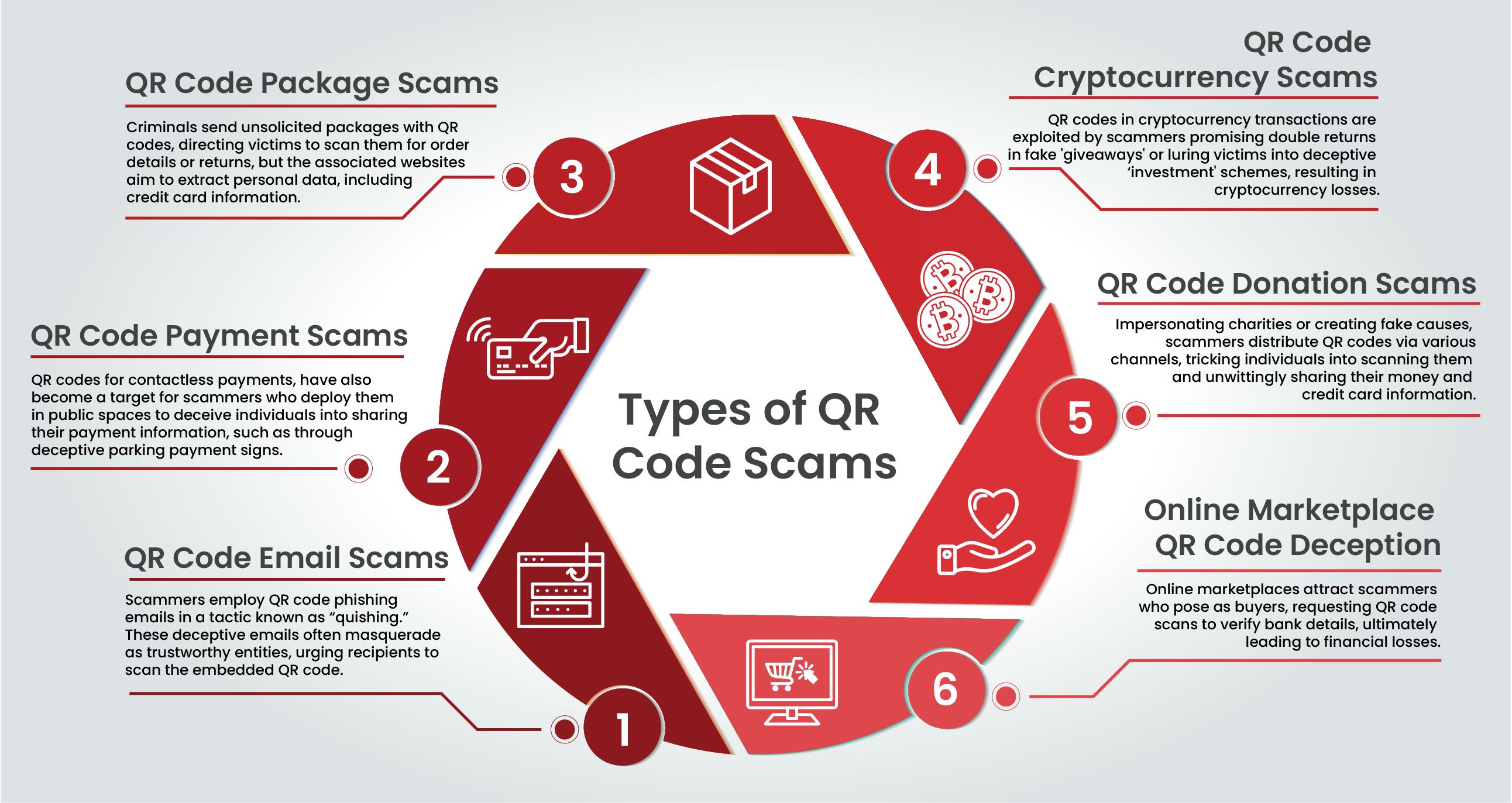
Known as “quishing,” scammers send phishing emails that impersonate trustworthy entities, urging recipients to scan an embedded QR code. For example, they may claim a recent online purchase payment failed and request users to resubmit their credit card details by scanning the QR code. Victims comply, landing on a convincing website where they unknowingly provide their credit card information to cybercriminals.
During the COVID-19 pandemic, QR codes became popular for contactless payments. Scammers exploit this by placing QR codes in public spaces to steal money or credit card data. For instance, deceptive signs in parking lots suggest paying for parking by scanning the QR code, which leads to a fraudulent website collecting payment information.
QR Code Package Scams
Receiving an unsolicited package with a QR code can be a scam. Criminals send unordered packages containing a QR code, prompting victims to scan it for order information or returns. The resulting website solicits personal data, including credit card numbers.
In cryptocurrency transactions, fraudsters may offer a supposed “giveaway,” promising double the cryptocurrency in exchange for an initial transfer. The promised crypto never materialises. Similarly, scammers lure victims into an “investment” scheme, soliciting cryptocurrency deposits before disappearing with the assets.
Scammers impersonate charities or fabricate fake causes, placing QR codes on flyers or sending them via text or email to solicit donations. Unsuspecting individuals scan these codes and contribute, unknowingly providing scammers with their money or credit card information.
Scammers on online marketplaces pose as prospective buyers, requesting sellers to scan a QR code to verify bank account details. This seemingly innocuous action grants scammers access to the seller’s bank account, resulting in monetary losses.
QR codes are everywhere, presenting significant security risks. To safeguard against cyber threats, adhere to the following QR code security best practices:
When using QR codes, vigilance is crucial. Be aware of potential red flags such as suspicious QR code placements, unexpected payment redirections, or requests for personal information. If anything seems unusual or too good to be true, refrain from scanning the code.
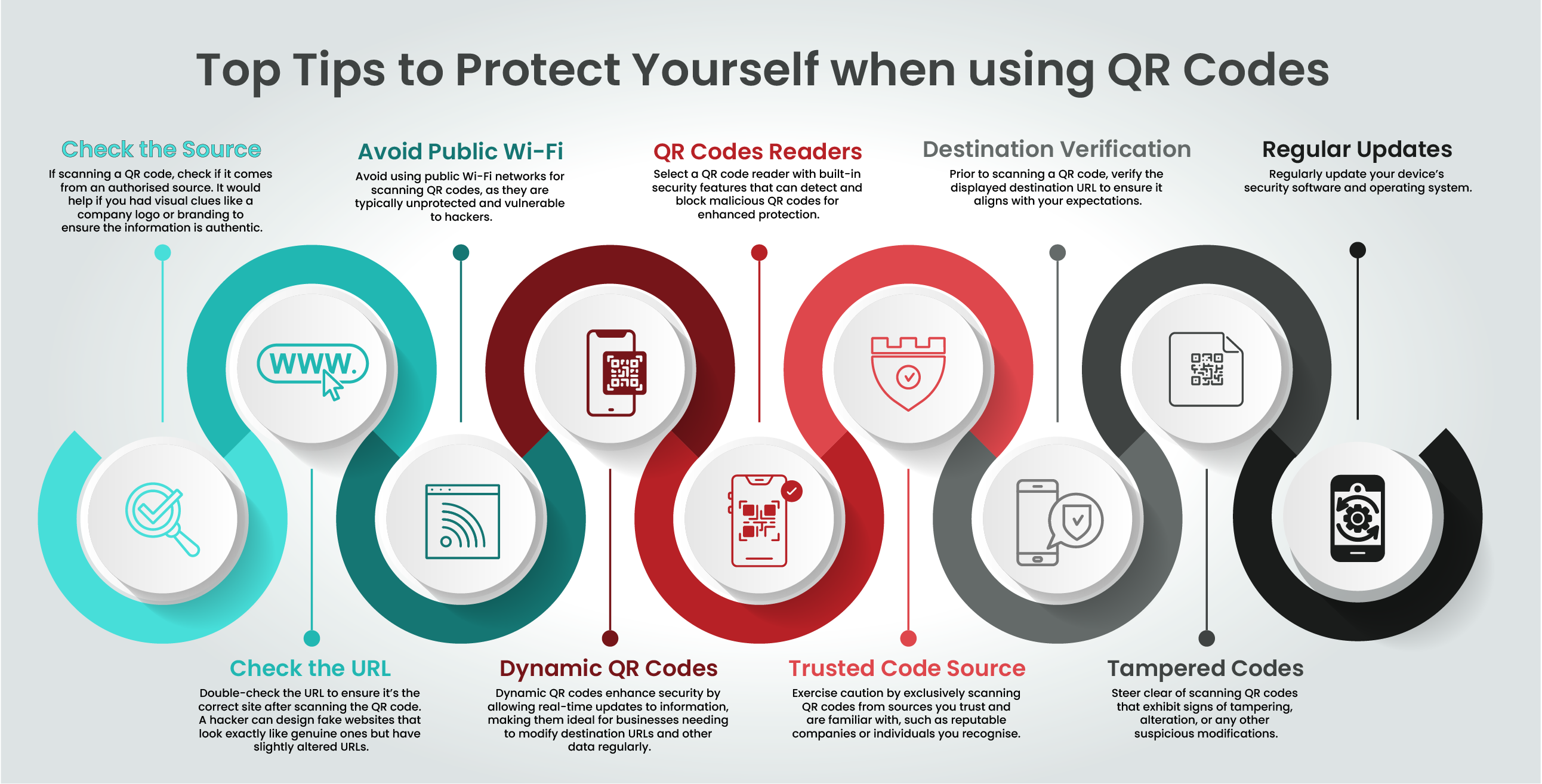
Ensure the QR code originates from a trustworthy and reputable source. Trusted sources are less likely to be associated with fraudulent codes.
After scanning, verify that the resulting URL matches the intended destination. Cybercriminals can create convincing fake websites with slightly altered URLs, so confirming authenticity is essential.
Avoid scanning QR codes while connected to public Wi-Fi networks, which are often less secure and more susceptible to hacking. Use a trusted and secure network to reduce the risk of encountering fraudulent QR codes.
Select QR code reader applications equipped with built-in security features designed to detect and block malicious QR codes, protecting your device and personal data.
Only scan QR codes from reputable and known sources to minimise the risk of encountering fraudulent or malicious codes.
Before scanning a QR code, verify the destination URL to ensure it leads to a legitimate and secure website. This simple step can help you avoid scams or phishing attempts.
Exercise caution and refrain from scanning QR codes that appear tampered with or altered, as they may harbour malicious intent.
Regularly update your devices, applications, and operating systems to stay protected against emerging threats. Updates often include patches for known vulnerabilities, strengthening your overall security posture.
Incorporating QR codes into your business strategy can enhance customer engagement and streamline operations. However, ensuring QR code security is vital. Here are our QR code security best practices to protect your business:
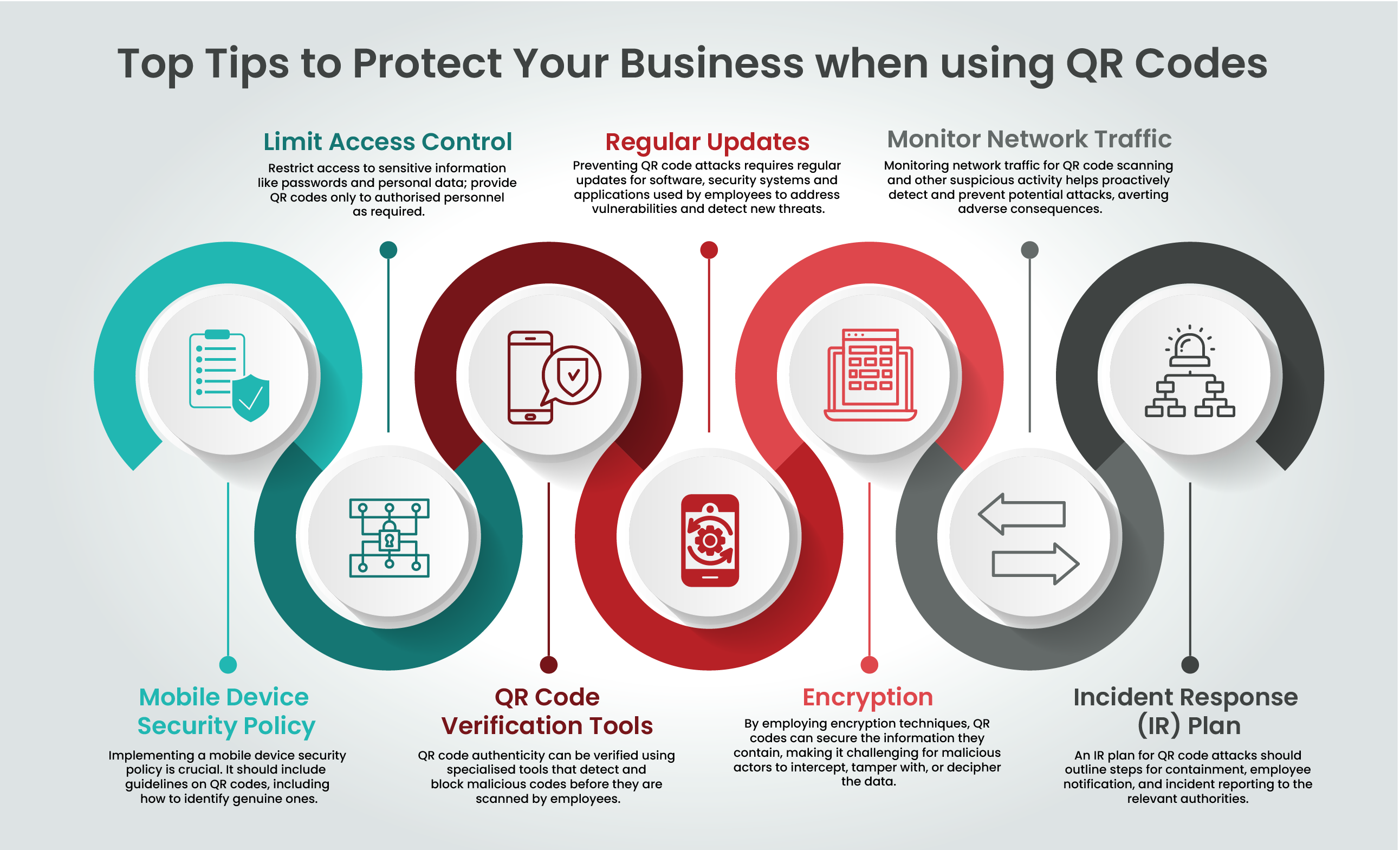
Establish a comprehensive mobile device security policy. This should include clear guidelines on the safe use and verification of QR codes. Educate employees to ensure consistent adherence to these security practices.
Restrict QR code access within your organisation to authorised personnel only. This minimises the risk of accidental exposure or misuse.
Deploy QR code verification tools to authenticate codes before scanning. These tools help prevent the scanning of malicious QR codes, protecting your business and stakeholders.
Keep your software, security systems, and applications up to date. Regular updates include critical security patches that enhance your overall security posture.
Encrypt data within QR codes to protect sensitive information. Encryption makes it difficult for unauthorised parties to access or manipulate data, safeguarding your business and customer information.
Continuously monitor network traffic for suspicious activities related to QR code scanning. Proactive detection and response can prevent security incidents from escalating.
Create a QR code-specific incident response (IR) plan. Outline steps for containing attacks, notifying affected parties, and reporting incidents to authorities. A well-defined IR plan ensures an effective response to security threats, minimising potential damage.
QR codes are widely used in consumer and business applications but pose security risks. Cybercriminals exploit them for phishing, malware, and other malicious activities. To mitigate these risks, users should verify the source and destination of QR codes, avoid public Wi-Fi, use dynamic QR codes, employ trusted readers, and keep devices updated.
Businesses should take it a step further by implementing a mobile device security policy, restricting access, using verification tools, ensuring regular software updates and encryption, monitoring network traffic, and having an incident response plan.
Understanding and addressing QR code security risks is essential. By following QR code security best practices, you can enjoy their convenience while protecting yourself and your business from cyber threats.
Ensuring the security of QR codes can be complex. Let us make it simple for you. Book a discovery call with our experts to learn how we can help protect your business from QR code-related threats effortlessly.
Cyber security shouldn’t be a headache. Get clear and actionable insights delivered straight to your inbox. We make complex threats understandable, empowering you to make informed decisions and protect your business.
Call us +44 20 8126 8620
Email us [email protected]